On Friday 12th May, organizations across the world were hit by a massive ransomware attack, named WannaCry, which exploited a (now patched) Microsoft Windows vulnerability revealed in the Shadowbrokers dump on April 14.
This latest variant of ransomware according to Avast Security data, is mainly being targeted to Russia, Ukraine and Taiwan, but the ransomware has successfully infected major institutions, like hospitals across England and Spanish telecommunications company, Telefonica.
The ransomware changes the affected file extension names to “.WNCRY”, so an infected file will look something like: original_name_of_file.jpg.WNCRY, for example. The encrypted files are also marked by the “WANACRY!” string at the beginning of the file.
The list of African countries affected by the WannaCry ransomware includes, but is not limited to, South Africa, Nigeria, Angola, Egypt, Mozambique, Tanzania, Niger, Morocco and Tunisia. This shows Africa was least hit in the aftermath of a global ransomware attack.
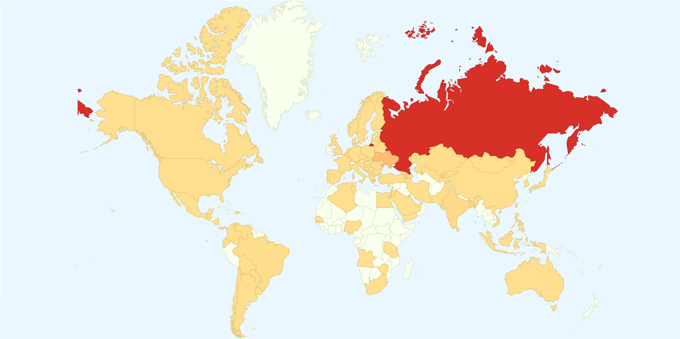
Below is a map showing the countries being targeted most by WannaCry:

Evolution of the ransomware according to Kaspersky
The total number of variants in circulation on Monday 15th is still unclear – but over the weekend two notable variants emerged. Kaspersky Lab does not believe any of these variants were created by the original authors – most likely they were patched by others keen to exploit the attack for their own ends.
The first one started spreading on Sunday morning, at around 02.00 UTC/GMT and was patched to connect to a different domain. Kaspersky Lab has so far noted three victims for this variant, located in Russia and Brazil.
The second variation that appeared during the weekend appears to have been patched to remove the killswitch. This variant does not appear to be spreading, possibly due to the fact it has a bug.
Kaspersky Lab advice to reduce the risk of infection
- Install the official patch from Microsoft that closes the vulnerability used in the attack (there are also patches available for Windows XP, Windows 8, and Windows Server 2003)
- Ensure that security solutions are switched on all nodes of the network
- For those who do not use Kaspersky Lab solutions, we suggest installing the free Kaspersky Anti-Ransomware Tool for business (KART).
- If Kaspersky Lab’s solution is used, ensure that it includes the System Watcher, a behavioral proactive detection component, and that it is switched on
- Run the Critical Area Scan task in Kaspersky Lab’s solution to detect possible infection as soon as possible (otherwise it will be detected automatically, if not switched off, within 24 hours).
- Reboot the system after detecting MEM: Trojan.Win64.EquationDrug.gen
- Use Customer-Specific Threat Intelligence Reporting services to be informed about possible attacks
- WannaCry is also targeting embedded systems. We recommend ensuring that dedicated security solutions for embedded systems are installed, and that they have both anti-malware protection and Default Deny functionality enabled.
