A security lapse has exposed a massive database containing tens of millions of text messages, including password reset links, two-factor codes, shipping notifications and more reports TechCrunch.
This is a Voxox (formerly Telcentris) server, a San Diego, Calif.-based communications company. The server wasn’t protected with a password, allowing anyone who knew where to look to peek in and snoop on a near-real-time stream of text messages.
For Sébastien Kaul, a Berlin-based security researcher, it didn’t take long to find.
Although Kaul found the exposed server on Shodan, a search engine for publicly available devices and databases, it was also attached to to one of Voxox’s own subdomains. Worse, the database — running on Amazon’s Elasticsearch — was configured with a Kibana front-end, making the data within easily readable, browsable and searchable for names, cell numbers and the contents of the text messages themselves.
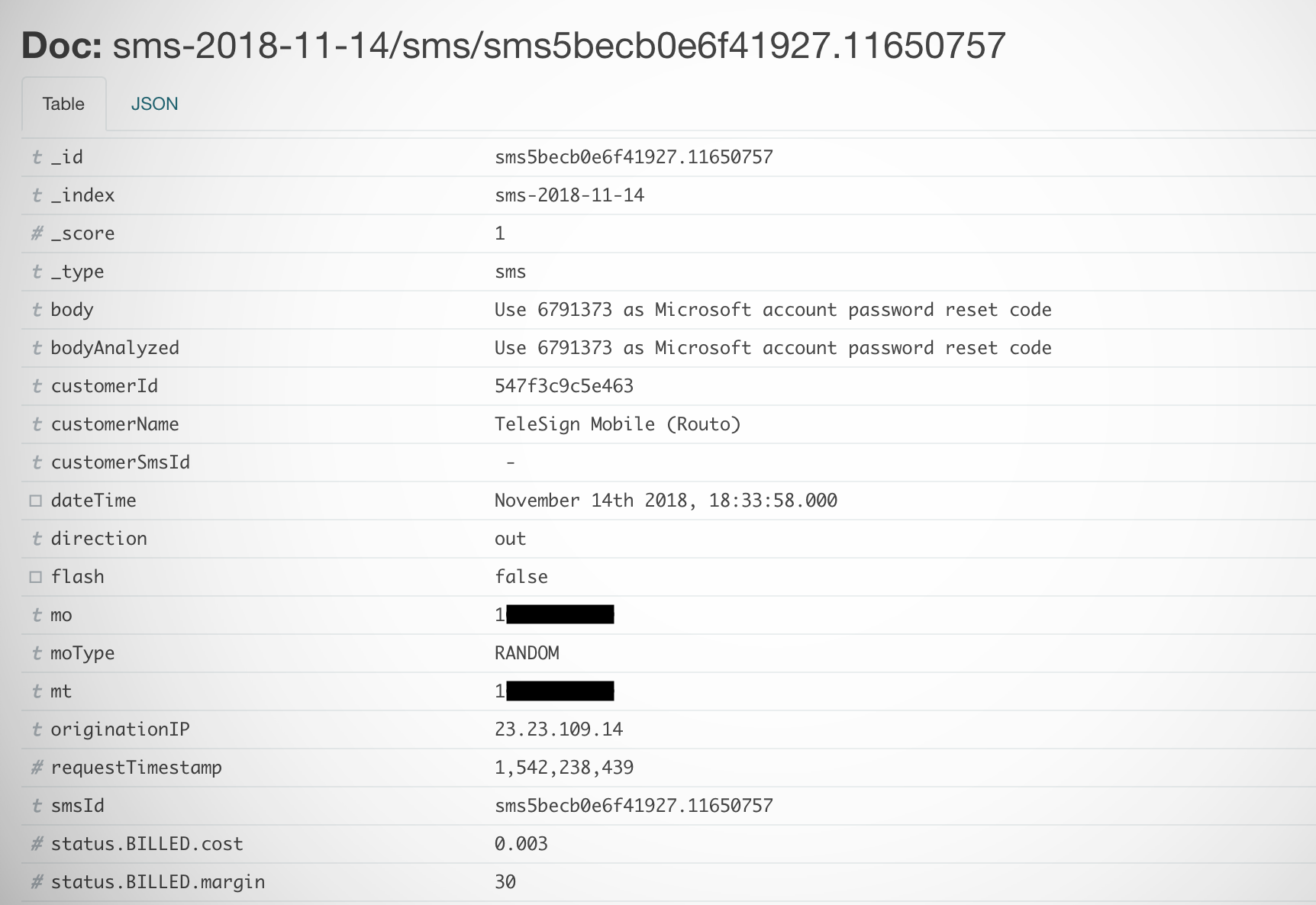

An example of one text message containing a user’s phone number and their Microsoft account reset code. (Image: TechCrunch)
Most don’t think about what happens behind the scenes when you get a text message from a company, whether it’s an Amazon shipping notification or a two-factor code for your login. Often, app developers — like HQ Trivia and Viber — will employ technologies provided by firms like Telesign and Nexmo, either to verify a user’s phone number or to send a two-factor authentication code, for example. But it’s firms like Voxox that act as a gateway and converting those codes into text messages, to be passed on to the cell networks for delivery to the user’s phone.
After an inquiry by TechCrunch, Voxox pulled the database offline. At the time of its closure, the database appeared to have a little over 26 million text messages year-to-date. But the sheer volume of messages processed through the platform per minute — as seen through the database’s visual front-end — suggests that this figure may be higher.
