Kaspersky Labs cybersecurity researchers have found an oddly amusing sample of ATM malware which turns financial theft into a slot machine-style game. On Tuesdaythe team explored the emergence of WinPot, an ATM hijacking malware family which first appeared in underground forums in March 2018.
While simple in its core functionality, WinPot — named internally by Kaspersky as ATMPot — is designed to compromise the ATMs of an unnamed but popular vendor and force these machines to empty their cassettes of all funds.
The interface of the malware is what makes the package unusual. Time has been spent on making the interface look like a slot machine, which is most likely a reference to “ATM jackpotting” — a term used to describe the compromise of ATMs themselves.
The interface includes a visual indicator of an ATM’s cassettes. Each one has a reel numbered 1 – 4, of which 4 is the maximum number of cash-out cassettes in a typical ATM.
A button labeled “spin,” when pressed, starts the dispensation of cash. The “stop” button cuts off cash from being spewed out, while “scan” resets the ‘game’ and re-scans a machine for cassette and fund availability.


Same as Cutler Maker, WinPot is available on the (Dark)net for approximately 500 – 1000 USD depending on offer.
One of the sellers offers WinPot v.3 together with a demo video depicting the “new” malware version along with a still unidentified program with the caption “ShowMeMoney”. Its looks and mechanics seem quite similar to those of the Stimulator from the CutletMaker story.
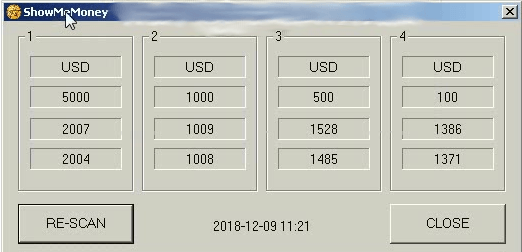

Unidentified Stimulator-like sample from demo video
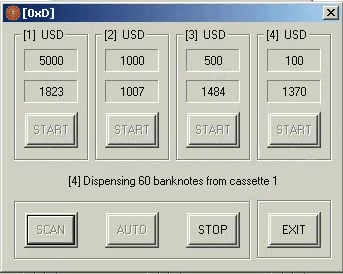

Winpot v3 sample from demo video
Due to the nature of ATM cash-out malware, its core functionality won’t change much. But criminals do encounter problems, so they invent modifications:
- To trick the ATM security systems (using protectors or other ways to make each new sample unique);
- To overcome potential ATM limitations (like maximum notes per dispense);
- To find ways to keep the money mules from abusing their malware;
- To improve the interface and error-handling routines.
We thus expect to see more modifications of the existing ATM malware. The preferred way of protecting the ATM from this sort of threat is to have device control and process whitelisting software running on it. The former will block the USB path of implanting the malware directly into the ATM PC, while the latter will prevent execution of unauthorized software on it. Kaspersky Embedded Systems Security will further help to improve the security level of the ATMs.
Kaspersky Lab products detect WinPot and its modifications as Backdoor.Win32.ATMPot.gen
Sample MD5:
821e593e80c598883433da88a5431e9d